React security Best Practices is a popular JavaScript library for building user interfaces, but with great power comes great responsibility. Security is critical when developing web applications to protect user data and maintain trust. This chapter will guide you through best practices for securing your React applications, from basic to advanced topics. We'll cover everything from common vulnerabilities to specific techniques to mitigate risks.
Understanding Common Vulnerabilities
Before diving into best practices, it’s essential to understand common security vulnerabilities that can affect React applications.
Cross-Site Scripting (XSS)
Description: XSS allows attackers to inject malicious scripts into webpages viewed by users. This can lead to session hijacking, data theft, and more.
Example: If user input is rendered directly in the DOM without sanitization, an attacker could inject a script.
const userInput = "<script type="litespeed/javascript">alert('Hacked!')</script>";
const UnsafeComponent = () => <div>{userInput}</div>; // Vulnerable to XSS
Cross-Site Request Forgery (CSRF)
Description: CSRF attacks occur when unauthorized commands are transmitted from a user that the web application trusts.
Injection Attacks
Description: Attackers can manipulate input to execute arbitrary commands or access unauthorized data. This includes SQL injection, command injection, etc.
React Security Best Practices for Securing React Applications
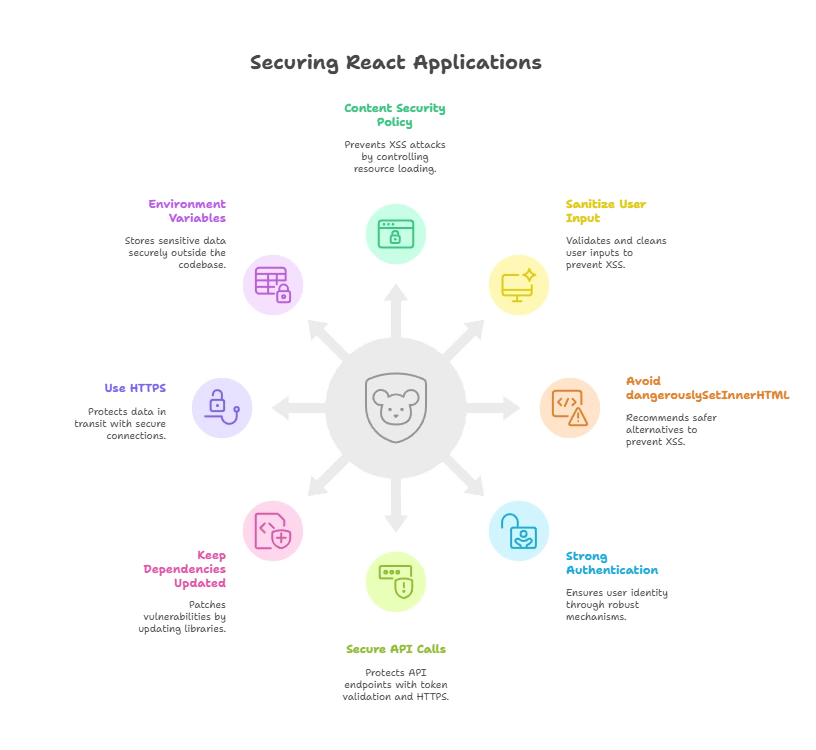
Use a Content Security Policy (CSP)
Description: CSP is a security feature that helps prevent XSS attacks by controlling which resources can be loaded.
Implementation: Add a CSP header to your server responses.
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted.cdn.com;
Sanitize User Input
Description: Always sanitize and validate user inputs to prevent XSS.
Example: Use libraries like dompurify to sanitize HTML.
npm install dompurify
import DOMPurify from 'dompurify';
const SafeComponent = ({ userInput }) => {
const sanitizedInput = DOMPurify.sanitize(userInput);
return <div dangerouslySetInnerHTML={{ __html: sanitizedInput }} />;
};
Avoid Using dangerouslySetInnerHTML
Description: This React feature allows you to set HTML directly, which can lead to XSS if misused. Avoid it unless absolutely necessary.
Example: Instead of using it, prefer using plain text or sanitized HTML.
const SafeText = ({ text }) => <div>{text}</div>; // Safe
Implement Strong Authentication and Authorization
Description: Use robust authentication mechanisms to ensure that users are who they say they are.
Example: Use libraries like jsonwebtoken for token-based authentication.
npm install jsonwebtoken
Example Code:
import jwt from 'jsonwebtoken';
const generateToken = (user) => {
return jwt.sign({ id: user.id }, 'your-secret-key', { expiresIn: '1h' });
};
Secure API Calls
Description: Ensure that your API endpoints are secure by validating tokens and using HTTPS.
Example:
const fetchData = async () => {
const response = await fetch('/api/data', {
method: 'GET',
headers: {
Authorization: `Bearer ${token}`,
},
});
const data = await response.json();
return data;
};
Keep Dependencies Updated
Description: Regularly update your libraries and frameworks to patch vulnerabilities.
Implementation: Use tools like npm audit or yarn audit.
npm audit fix
Use HTTPS
Description: Always serve your application over HTTPS to protect data in transit.
Implementation: Obtain an SSL certificate and configure your server to use HTTPS.
Use Environment Variables for Sensitive Data
Description: Never hardcode sensitive information in your codebase.
Example: Use .env files to store API keys and secrets.
REACT_APP_API_KEY=your_api_key_here
Access in Code:
const apiKey = process.env.REACT_APP_API_KEY;
Advanced Security Measures
Secure WebSocket Connections
Description: If your application uses WebSockets, ensure they are secure (wss://) and authenticate users properly.
Rate Limiting
Description: Implement rate limiting on your APIs to prevent abuse.
Logging and Monitoring
Description: Use logging to monitor activities in your application and identify potential security incidents.
Regular Security Audits
Description: Conduct regular security audits and penetration testing on your application.
Securing a React application requires diligence and adherence to best practices. By understanding common vulnerabilities and implementing recommended strategies, you can build a more secure application. Always stay updated on the latest security trends and keep learning to stay one step ahead of potential threats. Happy coding !❤️
