Handling TLS/SSL Connections
Transport Layer Security (TLS), and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols designed to provide secure communication over a computer network. TLS/SSL protocols ensure that data transmitted between a client and a server remains private and integral. In this chapter, we'll delve into how to handle TLS/SSL connections in Go, starting from the fundamentals to more advanced topics.
Basics of TLS/SSL
What is TLS/SSL?
TLS/SSL protocols encrypt the data transmitted between a client and a server, preventing eavesdropping and tampering by malicious actors. They use asymmetric encryption for key exchange and symmetric encryption for data encryption, providing a secure communication channel.
TLS Handshake Process
The TLS handshake is a crucial step in establishing a secure connection between a client and a server. It involves multiple steps, including negotiating encryption algorithms, exchanging cryptographic keys, and verifying the authenticity of the server’s certificate.
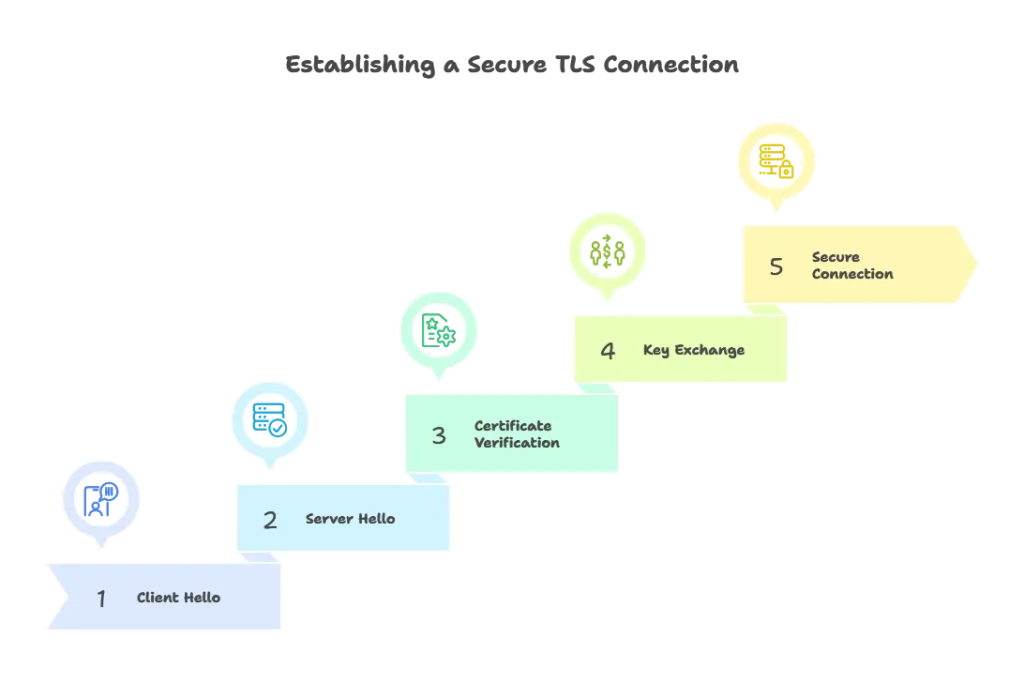
Implementing TLS/SSL in Go
Setting Up a TLS Server
Let’s start by creating a basic TLS server in Go using the net/http package
package main
import (
"fmt"
"net/http"
)
func handler(w http.ResponseWriter, r *http.Request) {
fmt.Fprintf(w, "Welcome to the secure server!")
}
func main() {
http.HandleFunc("/", handler)
err := http.ListenAndServeTLS(":443", "server.crt", "server.key", nil)
if err != nil {
fmt.Println("Error starting server:", err)
}
}
- We define an HTTP handler function to handle incoming requests.
- In the
mainfunction, we usehttp.ListenAndServeTLSto start a secure HTTP server. We provide the paths to the server certificate (server.crt) and private key (server.key).
Advanced TLS Configuration
Customizing TLS Configuration
In some scenarios, you may need to fine-tune the TLS configuration of your server to meet specific security requirements or to ensure compatibility with clients. Let’s delve deeper into the various parameters you can customize and their implications.
Minimum and Maximum TLS Versions
TLS supports multiple versions, including TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3. By specifying the minimum and maximum TLS versions supported by your server, you can control the negotiation process and ensure compatibility with clients.
TLSConfig: &tls.Config{
MinVersion: tls.VersionTLS12,
MaxVersion: tls.VersionTLS13,
},
In this example, we’ve configured the server to support TLS 1.2 and TLS 1.3, excluding older versions for security reasons.
Cipher Suites
Cipher suites determine the encryption algorithms used for securing the TLS connection. While modern cipher suites provide stronger security, they may not be supported by older clients. You can specify the preferred cipher suites for your server to strike a balance between security and compatibility.
TLSConfig: &tls.Config{
CipherSuites: []uint16{
tls.TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,
tls.TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,
},
},
In this example, we’ve selected two widely supported cipher suites: AES with 256-bit and 128-bit keys in Galois Counter Mode (GCM) with SHA-384 and SHA-256 hash functions, respectively.
Certificate Verification
Certificate verification is crucial for ensuring the authenticity of the server’s certificate and preventing man-in-the-middle attacks. By default, Go’s TLS library performs certificate verification. However, you can customize the verification process to implement additional checks, such as hostname validation.
TLSConfig: &tls.Config{
// Enable server certificate verification
ClientAuth: tls.RequireAndVerifyClientCert,
// Customize certificate validation function
VerifyPeerCertificate: func(rawCerts [][]byte, verifiedChains [][]*x509.Certificate) error {
// Implement custom certificate validation logic
return nil
},
},
In this example, we’ve enabled client certificate verification (tls.RequireAndVerifyClientCert) and provided a custom function (VerifyPeerCertificate) for validating peer certificates. You can implement your validation logic based on your security requirements.
Session Resumption
TLS session resumption allows clients and servers to reuse previously established sessions, reducing the overhead of cryptographic negotiations and improving performance. You can enable session resumption by configuring session ticket keys and enabling session ticket resumption.
TLSConfig: &tls.Config{
// Enable session ticket resumption
SessionTicketsDisabled: false,
// Configure session ticket keys
SessionTicketKeys: [][]byte{ /* Session ticket keys */ },
},
In this example, we’ve selected two widely supported cipher suites: AES with 256-bit and 128-bit keys in Galois Counter Mode (GCM) with SHA-384 and SHA-256 hash functions, respectively.
Client-side TLS Communication
TLS Client in Go
While we’ve explored setting up a TLS server, it’s equally important to understand how to create TLS clients in Go to establish secure connections with servers.
package main
import (
"crypto/tls"
"fmt"
"io/ioutil"
"net/http"
)
func main() {
// Create a TLS configuration
tlsConfig := &tls.Config{
InsecureSkipVerify: true, // InsecureSkipVerify should be set to false in production for proper certificate validation
}
// Create an HTTP client with the TLS configuration
client := &http.Client{
Transport: &http.Transport{
TLSClientConfig: tlsConfig,
},
}
// Send a GET request to the server
resp, err := client.Get("https://example.com")
if err != nil {
fmt.Println("Error:", err)
return
}
defer resp.Body.Close()
// Read the response body
body, err := ioutil.ReadAll(resp.Body)
if err != nil {
fmt.Println("Error reading response body:", err)
return
}
// Print the response body
fmt.Println(string(body))
}
- We create a custom TLS configuration with
InsecureSkipVerifyset to true for simplicity. In a real-world scenario, this should be set to false to enable proper certificate validation. - We create an HTTP client with the custom TLS configuration.
- The client sends a GET request to the server (in this case, “https://example.com“).
- We read and print the response body.
Certificate Management
Generating Self-Signed Certificates
In development or testing environments, you may need to generate self-signed certificates for testing TLS connections. Go provides a utility called openssl for generating self-signed certificates.
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365
- This command generates a self-signed certificate (
cert.pem) and a private key (key.pem) valid for 365 days.
Using Let’s Encrypt for Production Certificates
For production use, it’s recommended to obtain certificates from a trusted Certificate Authority (CA) like Let’s Encrypt. Go provides libraries like acme/autocert for automatically obtaining and managing certificates from Let’s Encrypt.
package main
import (
"crypto/tls"
"net/http"
"golang.org/x/crypto/acme/autocert"
)
func main() {
m := &autocert.Manager{
Prompt: autocert.AcceptTOS,
HostPolicy: autocert.HostWhitelist("example.com"),
Cache: autocert.DirCache("/var/www/.cache"),
}
server := &http.Server{
Addr: ":443",
TLSConfig: &tls.Config{
GetCertificate: m.GetCertificate,
},
}
server.ListenAndServeTLS("", "")
}
- We use
autocert.Managerto manage certificates from Let’s Encrypt. - We specify the domain name (
example.com) for which we want to obtain certificates. - We set the cache directory for storing obtained certificates.
In this comprehensive chapter, we've covered various aspects of handling TLS/SSL connections in Go, from setting up basic TLS servers to configuring advanced TLS options, managing TLS clients, and dealing with certificates. By mastering TLS in Go, you can ensure secure communication in your applications, protecting sensitive data and maintaining the integrity of your systems. Experiment with different configurations, explore additional TLS features, and always prioritize security best practices in your development efforts. Happy coding !❤️
