Preventing Injection Attacks (SQL Injection, XSS) in Go
In this chapter, we'll explore the importance of preventing injection attacks, such as SQL injection and Cross-Site Scripting (XSS), in Go applications. We'll cover various techniques and best practices for mitigating these vulnerabilities to ensure the security of your web applications.
Understanding Injection Attacks
Introduction to Injection Attacks
Injection attacks occur when an attacker injects malicious code or commands into an application’s input fields, exploiting vulnerabilities to execute arbitrary code or gain unauthorized access to data. Two common types of injection attacks are SQL injection and Cross-Site Scripting (XSS).
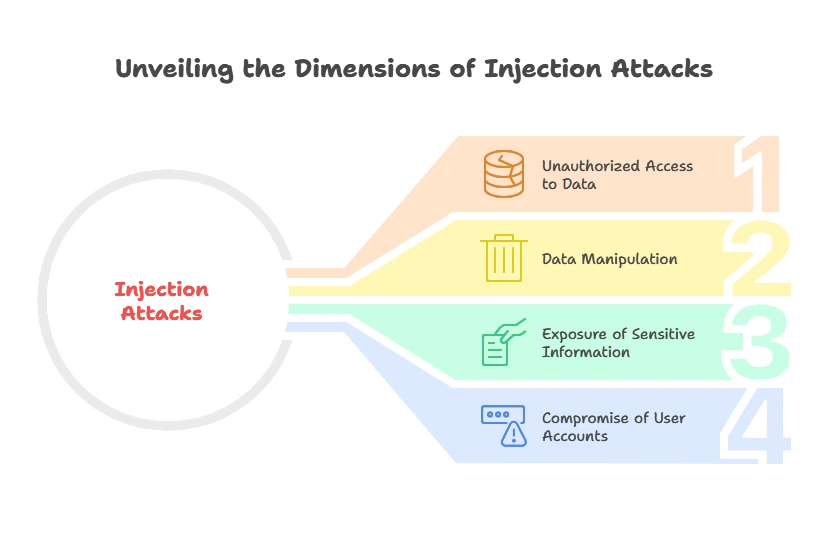
Risks of Injection Attacks
Injection attacks can lead to severe consequences, including:
- Unauthorized access to sensitive data.
- Manipulation or deletion of data.
- Exposure of sensitive information.
- Compromise of user accounts or sessions.
Preventing SQL Injection in Go
Parameterized Queries
Parameterized queries (also known as prepared statements) help prevent SQL injection attacks by separating SQL logic from user input. Go’s database/sql package supports parameterized queries, making it easy to implement this security measure.
package main
import (
"database/sql"
"fmt"
_ "github.com/go-sql-driver/mysql"
)
func main() {
db, err := sql.Open("mysql", "user:password@/database")
if err != nil {
panic(err.Error())
}
defer db.Close()
// Prepare statement
stmt, err := db.Prepare("SELECT * FROM users WHERE username = ? AND password = ?")
if err != nil {
panic(err.Error())
}
defer stmt.Close()
// Execute query with user input as parameters
rows, err := stmt.Query("userInput", "userInputPassword")
if err != nil {
panic(err.Error())
}
defer rows.Close()
// Process query results
for rows.Next() {
// Process each row
}
}
Input Validation and Sanitization
Validate and sanitize user input to ensure it meets expected criteria and does not contain malicious content. Use validation libraries or custom validation functions to sanitize input before processing it.
package main
import (
"fmt"
"github.com/go-playground/validator"
)
type User struct {
Username string `validate:"required"`
Password string `validate:"required"`
}
func main() {
// Create a new instance of the validator
validate := validator.New()
// Validate user input
user := User{Username: "", Password: "password123"}
err := validate.Struct(user)
if err != nil {
fmt.Println("Validation error:", err)
return
}
// Proceed with processing user input
}
Preventing Cross-Site Scripting (XSS) in Go
HTML Escaping
HTML escaping (or encoding) involves converting special characters into their corresponding HTML entities, preventing them from being interpreted as code by the browser. Go’s html/template package provides functions for HTML escaping.
package main
import (
"html/template"
"os"
)
func main() {
// Create a new template
tmpl := template.New("example")
// Define the template content
tmplContent := "<h1>{{.Title}}</h1><p>{{.Content}}</p>"
// Parse the template
tmpl, err := tmpl.Parse(tmplContent)
if err != nil {
panic(err)
}
// Define data
data := struct {
Title string
Content string
}{
Title: "<script type="litespeed/javascript">alert('XSS attack!')</script>",
Content: "This is a safe content.",
}
// Execute the template with HTML escaping
err = tmpl.Execute(os.Stdout, data)
if err != nil {
panic(err)
}
}
Content Security Policy (CSP)
Content Security Policy (CSP) is a security standard that helps prevent XSS attacks by defining and enforcing a set of rules for permitted content sources. Implement CSP headers in your Go application to restrict the types of content that browsers can load.
package main
import (
"net/http"
)
func main() {
http.HandleFunc("/", func(w http.ResponseWriter, r *http.Request) {
w.Header().Set("Content-Security-Policy", "default-src 'self'")
// Other handler logic...
})
http.ListenAndServe(":8080", nil)
}
In conclusion, preventing injection attacks such as SQL injection and Cross-Site Scripting (XSS) is crucial for maintaining the security of your Go applications. By implementing measures like parameterized queries, input validation, HTML escaping, and Content Security Policy (CSP), you can effectively mitigate these vulnerabilities and protect your application and users from malicious attacks. Always stay vigilant and keep your application's security practices up-to-date to defend against evolving threats. Happy coding !❤️
