Configuring SSL/TLS for Secure Communication
In today’s world, securing data in transit is crucial to protect sensitive information from unauthorized access. SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are encryption protocols that secure communication channels over networks, ensuring that data exchanged between MongoDB clients and servers remains confidential and protected.
Introduction to SSL/TLS
What is SSL/TLS?
SSL and its successor, TLS, are cryptographic protocols used to secure communications over networks. They provide:
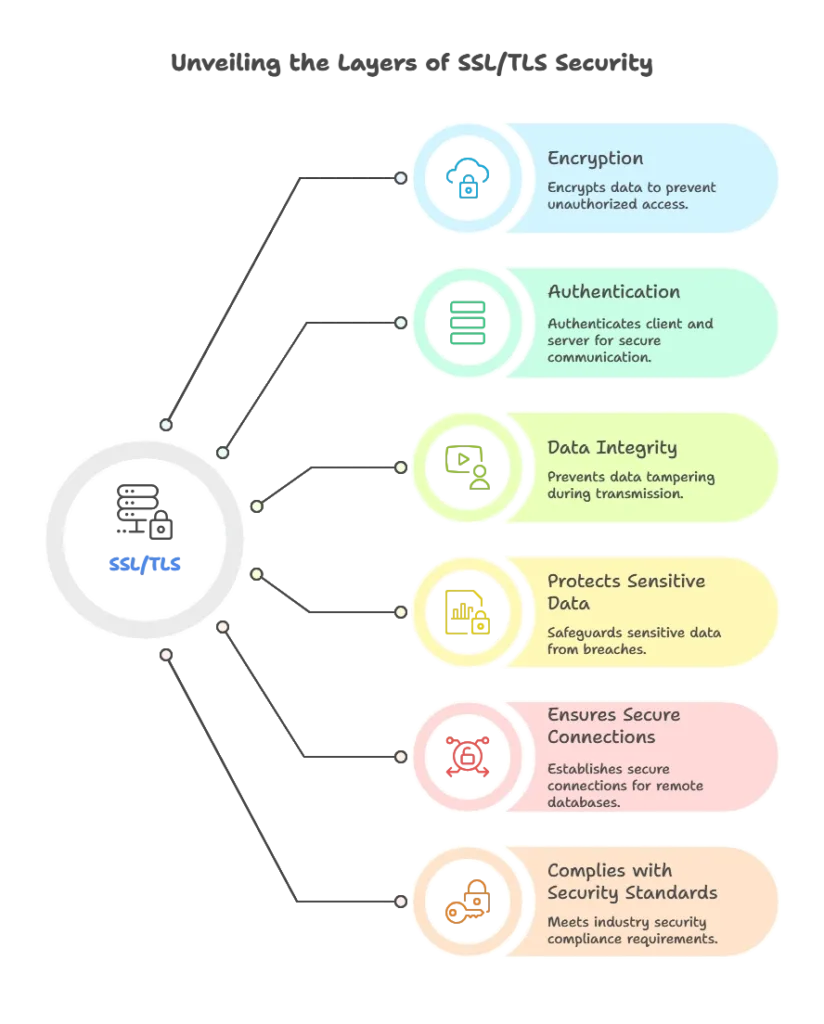
- Encryption: Data transferred over the network is encrypted, preventing unauthorized parties from reading it.
- Authentication: Both client and server can authenticate each other to ensure they are communicating with legitimate entities.
- Data Integrity: SSL/TLS prevents data from being tampered with during transit.
Why Use SSL/TLS in MongoDB?
Using SSL/TLS in MongoDB:
- Protects Sensitive Data: By encrypting data in transit, SSL/TLS helps prevent data breaches.
- Complies with Security Standards: Many industries require encrypted data transmissions.
- Ensures Secure Connections: Secure communication between distributed systems, especially for remote databases.
Preparing SSL/TLS Certificates
MongoDB uses certificates to validate secure connections. For testing, you can generate self-signed certificates; however, for production environments, use certificates from a trusted Certificate Authority (CA).
Generating a Self-Signed Certificate (For Testing Purposes)
1. Generate a Private Key and Certificate: Use OpenSSL to create a private key and a self-signed certificate for MongoDB.
openssl req -newkey rsa:4096 -nodes -keyout mongodb.key -x509 -days 365 -out mongodb.crt
-newkey rsa:4096: Generates a new RSA key with a 4096-bit key length.-keyout mongodb.key: Outputs the private key tomongodb.key.-x509: Specifies that this is a self-signed certificate.-days 365: The certificate is valid for 365 days.
2. Combine Key and Certificate: MongoDB requires the key and certificate in one .pem file.
cat mongodb.key mongodb.crt > mongodb.pem
chmod 600 mongodb.pem
The mongodb.pem file now contains both the private key and the certificate.
Configuring MongoDB for SSL/TLS
Once the SSL/TLS certificates are ready, the next step is to configure MongoDB to use these certificates.
Editing the MongoDB Configuration File
1. Locate the Configuration File: MongoDB configuration is often in /etc/mongod.conf on Linux systems or C:\Program Files\MongoDB\Server\<version>\bin\mongod.cfg on Windows.
2. Add SSL/TLS Settings: Update the configuration file to enable SSL/TLS and specify the certificate file path.
net:
ssl:
mode: requireSSL
PEMKeyFile: /path/to/mongodb.pem
mode: requireSSL: Enforces SSL/TLS for all client-server communications.PEMKeyFile: Specifies the path to the.pemfile containing the certificate and private key.
Restart the MongoDB Server: Restart the MongoDB instance to apply the changes.
sudo systemctl restart mongod
Understanding SSL Modes in MongoDB
MongoDB offers different SSL modes based on the security requirements:
- disabled: SSL/TLS is completely disabled.
- allowSSL: Clients can connect with or without SSL.
- preferSSL: SSL connections are preferred, but non-SSL connections are allowed.
- requireSSL: Only SSL connections are accepted (recommended for production).
Connecting to MongoDB with SSL/TLS Enabled
After configuring MongoDB to require SSL/TLS, you need to connect using clients configured for SSL.
Connecting with the Mongo Shell
To connect using the Mongo shell with SSL:
mongo --host <hostname> --ssl --sslCAFile /path/to/mongodb.crt
--ssl: Enables SSL/TLS for the connection.--sslCAFile: Specifies the certificate file used to validate the server.
If using a self-signed certificate, add --sslAllowInvalidCertificates for testing purposes:
mongo --host <hostname> --ssl --sslCAFile /path/to/mongodb.crt --sslAllowInvalidCertificates
Connecting with MongoDB Clients (e.g., Node.js)
To connect to an SSL-enabled MongoDB instance in a Node.js application, add SSL options in the MongoDB connection string.
const { MongoClient } = require('mongodb');
const url = "mongodb://<username>:<password>@<hostname>:27017/?ssl=true&tlsCAFile=/path/to/mongodb.crt";
const client = new MongoClient(url, { useNewUrlParser: true, useUnifiedTopology: true });
async function connect() {
try {
await client.connect();
console.log("Connected to MongoDB with SSL/TLS!");
} finally {
await client.close();
}
}
connect();
Advanced SSL/TLS Configurations
Client Certificate Validation (Mutual SSL Authentication)
Mutual SSL authentication ensures that both the client and server authenticate each other, enhancing security.
1. Generate Client Certificates: Follow similar steps as above to generate client certificates.
2. Configure MongoDB for Mutual SSL: Add client certificate validation in the MongoDB configuration file.
net:
ssl:
mode: requireSSL
PEMKeyFile: /path/to/mongodb.pem
CAFile: /path/to/ca.crt
clusterAuthMode: x509
Connect Using Client Certificate: In the Mongo shell, specify the client certificate:
mongo --host <hostname> --ssl --sslCAFile /path/to/ca.crt --sslPEMKeyFile /path/to/client.pem
Configuring SSL/TLS with Replica Sets and Sharded Clusters
For a secure MongoDB deployment with replica sets or sharded clusters, all nodes need SSL/TLS enabled.
1. Enable SSL/TLS on Each Node: Follow the steps above to enable SSL on each MongoDB instance.
2. Specify Cluster Authentication Mode: Use clusterAuthMode: x509 in your configuration file to enforce SSL/TLS authentication within the cluster.
3. Connect Replica Set Members Using SSL/TLS: Ensure each member of the replica set or shard is configured to communicate over SSL/TLS.
Testing SSL/TLS Configurations
Testing your SSL/TLS configuration is crucial to ensure that the encryption setup works as expected.
Verifying the SSL Connection in MongoDB Logs
Upon successfully configuring SSL/TLS, MongoDB logs will show connection messages indicating SSL use. You can view these logs in /var/log/mongodb/mongod.log (Linux) or mongod.log (Windows).
Testing for Encrypted Traffic
Use tools like Wireshark to monitor network traffic and verify that data between MongoDB clients and the server is encrypted.
Securing MongoDB communication with SSL/TLS is essential for protecting data in transit. This chapter covered the process from generating certificates to configuring and testing SSL/TLS connections in MongoDB, including advanced setups for mutual SSL and replica sets. Happy Coding!❤️
