Security Best practices
In today's digital landscape, security is a critical concern for any web application. Express.js, as one of the most popular Node.js frameworks, provides powerful tools and flexibility to build web applications. However, with great power comes great responsibility—securing your Express.js applications is paramount. This chapter will guide you through the best practices to secure your Express.js applications from common threats, from basic security concepts to advanced techniques. We'll cover everything you need to know, with practical examples and explanations.
Understanding Security Threats
Common Web Application Threats
Before diving into the best practices, it’s essential to understand the types of threats that can target web applications:
- Cross-Site Scripting (XSS): An attacker injects malicious scripts into web pages viewed by other users.
- Cross-Site Request Forgery (CSRF): An attacker tricks a user into performing an action they didn’t intend to, by exploiting their authenticated session.
- SQL Injection: Malicious SQL code is inserted into queries, allowing attackers to manipulate the database.
- Denial of Service (DoS) Attacks: Overwhelming the application with traffic to make it unavailable to legitimate users.
- Man-in-the-Middle (MitM) Attacks: Intercepting communications between two parties to steal or alter data.
Understanding these threats is the first step toward mitigating them.
Express.js, being a minimalist framework, doesn’t come with built-in security features for every potential threat. However, it provides the flexibility to integrate security practices and tools. As a developer, you are responsible for implementing these practices to protect your application.
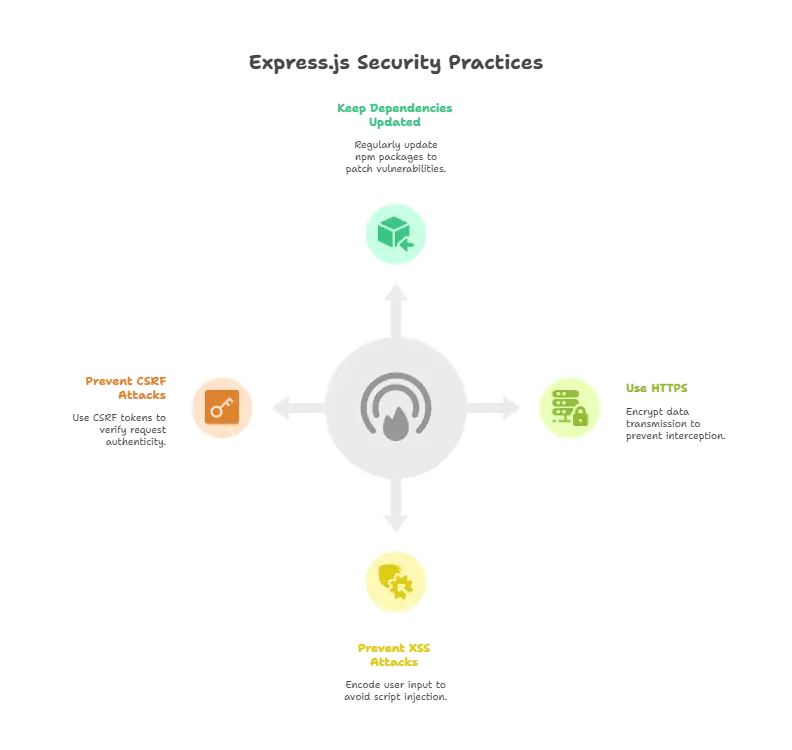
Keep Your Dependencies Updated
Using outdated dependencies is one of the most common vulnerabilities in web applications. Express.js applications often rely on multiple npm packages, and vulnerabilities in any of them can expose your application to risks.
Steps to Keep Dependencies Updated:
- Use npm audit: Regularly run
npm auditto check for vulnerabilities in your dependencies. - Update Dependencies: Use
npm updateto update packages. Be cautious with major updates, as they might introduce breaking changes. - Monitor Vulnerabilities: Consider using tools like Snyk to monitor for vulnerabilities continuously.
Example:
# Check for vulnerabilities
npm audit
# Update packages
npm update
Use HTTPS
HTTPS encrypts the data transmitted between the client and server, preventing attackers from intercepting or altering it. Always use HTTPS in production environments.
Steps to Enable HTTPS:
- Obtain an SSL/TLS Certificate: Get a certificate from a trusted Certificate Authority (CA) or use Let’s Encrypt for free certificates.
- Configure Express.js to Use HTTPS:
File: app.js
const express = require('express');
const https = require('https');
const fs = require('fs');
const path = require('path');
const app = express();
// Load SSL certificate and private key
const options = {
key: fs.readFileSync(path.join(__dirname, 'cert', 'private.key')),
cert: fs.readFileSync(path.join(__dirname, 'cert', 'certificate.crt'))
};
// Define a simple route
app.get('/', (req, res) => {
res.send('Hello, secure world!');
});
// Start HTTPS server
https.createServer(options, app).listen(3000, () => {
console.log('Server running on https://localhost:3000');
});
Explanation:
- The SSL certificate (
certificate.crt) and private key (private.key) are loaded to start an HTTPS server. - Ensure that all traffic is redirected from HTTP to HTTPS.
Preventing XSS Attacks
Cross-Site Scripting (XSS) attacks occur when an attacker injects malicious scripts into your web pages. These scripts can steal sensitive data or perform unauthorized actions.
Mitigation Techniques:
- Use Output Encoding: Always encode user input before displaying it on the page.
- Use a Content Security Policy (CSP): Restrict the sources from which your application can load scripts.
File: app.js (continued)
const helmet = require('helmet');
// Use Helmet to set security-related HTTP headers
app.use(helmet());
// Example of rendering user input safely
app.get('/profile', (req, res) => {
const username = req.query.username;
// Safely output user input
res.send(`Hello, ${escapeHtml(username)}!`);
});
// Function to escape HTML characters
function escapeHtml(text) {
return text.replace(/[&<>"']/g, function(match) {
const escape = {
'&': '&',
'<': '<',
'>': '>',
'"': '"',
"'": '''
};
return escape[match];
});
}
Explanation:
- Helmet: Helmet is a middleware that helps secure your Express.js application by setting various HTTP headers, including CSP.
- Escape HTML: Always escape special characters in user input to prevent XSS.
Preventing CSRF Attacks
Cross-Site Request Forgery (CSRF) attacks trick users into performing actions they didn’t intend to, by exploiting their authenticated session.
Mitigation Techniques:
- Use CSRF Tokens: Generate a unique token for each session and verify it with every state-changing request.
File: app.js (continued)
const csrf = require('csurf');
// Set up CSRF protection middleware
const csrfProtection = csrf({ cookie: true });
const parseForm = bodyParser.urlencoded({ extended: false });
app.use(cookieParser());
// Route with CSRF protection
app.get('/form', csrfProtection, (req, res) => {
// Send the form with a CSRF token
res.send(`
<form action="/submit" method="POST">
<input type="hidden" name="_csrf" value="${req.csrfToken()}" />
<div>
<label>Data:</label>
<input type="text" name="data" />
</div>
<button type="submit">Submit</button>
</form>
`);
});
app.post('/submit', parseForm, csrfProtection, (req, res) => {
res.send('Form submitted successfully!');
});
Explanation:
- CSRF Middleware: The
csurfmiddleware generates and validates CSRF tokens, ensuring that requests are genuine and not forged. - CSRF Token in Form: The token is embedded in forms and must be submitted with the form data, ensuring the request is legitimate.
Advanced Security Practices in Express.js
Rate Limiting to Prevent DoS Attacks
Denial of Service (DoS) attacks aim to overwhelm your application with requests, making it unavailable to legitimate users. Implementing rate limiting can mitigate this risk.
Mitigation Techniques:
- Use Rate Limiting Middleware: Limit the number of requests a client can make in a given time frame.
File: app.js (continued)
const rateLimit = require('express-rate-limit');
// Apply rate limiting to all requests
const limiter = rateLimit({
windowMs: 15 * 60 * 1000, // 15 minutes
max: 100, // Limit each IP to 100 requests per windowMs
message: 'Too many requests, please try again later.'
});
app.use(limiter);
Explanation:
- Rate Limiting: The
express-rate-limitmiddleware is configured to allow a maximum of 100 requests per 15 minutes per IP address. This prevents abuse and protects your application from being overwhelmed by requests.
Secure Session Management
Sessions are used to store user information between HTTP requests. Ensuring sessions are managed securely is vital to prevent unauthorized access.
Mitigation Techniques:
- Use Secure, HttpOnly Cookies: Ensure session cookies are not accessible via JavaScript.
- Set a Short Session Expiry: Limit the lifespan of session cookies to reduce the risk of hijacking.
File: app.js (continued)
const session = require('express-session');
app.use(session({
secret: 'your-secret-key',
resave: false,
saveUninitialized: true,
cookie: {
secure: true, // Ensure the cookie is sent only over HTTPS
httpOnly: true, // Prevents client-side JavaScript from accessing the cookie
maxAge: 60000 // Session expires in 1 minute
}
}));
Explanation:
- Session Security: The session is stored in a cookie that is marked as
secure(only sent over HTTPS) andhttpOnly(not accessible via JavaScript). ThemaxAgelimits the session duration, reducing the risk of session hijacking.
Implementing Input Validation and Sanitization
Input validation and sanitization ensure that the data entering your application is what you expect, preventing attacks such as SQL Injection and XSS.
Mitigation Techniques:
- Use a Validation Library: Validate and sanitize user input before processing it.
File: app.js (continued)
const { body, validationResult } = require('express-validator');
app.post('/register', [
body('username').isAlphanumeric().withMessage('Username must be alphanumeric'),
body('email').isEmail().withMessage('Invalid email address'),
body('password').isLength({ min: 5 }).withMessage('Password must be at least 5 characters long')
], (req, res) => {
const errors = validationResult(req);
if (!errors.isEmpty()) {
return res.status(400).json({ errors: errors.array() });
}
res.send('User registered successfully!');
});
Explanation:
- Validation: The
express-validatorlibrary is used to ensure that theusernameis alphanumeric, theemailis a valid email address, and thepasswordmeets the minimum length requirement. Any validation errors are returned to the user, preventing invalid data from being processed.
Security Tools and Libraries
Helmet
Helmet helps secure your Express.js application by setting various HTTP headers, such as Content Security Policy (CSP), X-Content-Type-Options, and more.
File: app.js (continued)
const helmet = require('helmet');
// Use Helmet to enhance security
app.use(helmet());
Explanation:
- Helmet Middleware: By adding
helmet(), your application gains additional layers of security through HTTP headers, protecting against a wide range of attacks.
Using Express.js Security Best Practices
Express.js provides a robust foundation for building secure web applications, but implementing best practices is crucial. Here are some recommendations:
- Content Security Policy (CSP): Use CSP to restrict sources for loading scripts, styles, and other resources.
- Disable X-Powered-By Header: Hide the fact that your application is using Express.js by disabling the
X-Powered-Byheader.
File: app.js (continued)
app.disable('x-powered-by');
Explanation:
- Hiding Express.js: Disabling the
X-Powered-Byheader makes it harder for attackers to determine what technology your application is using, reducing the risk of targeted attacks.
Key takeways
- Keeping dependencies up to date.
- Using HTTPS for secure communication.
- Preventing common web application threats such as XSS and CSRF.
- Implementing rate limiting, secure session management, and input validation.
- Leveraging security tools like Helmet and implementing security headers.
Securing your Express.js application is an ongoing process. Regularly review your security measures, keep up with the latest security updates, and continuously test your application for vulnerabilities. Security is not just about implementing the right tools but also about maintaining a security-conscious mindset throughout the development lifecycle. Happy coding !❤️
